Encryption and Privacy V: The key as personal data
The public key of a natural person is a unique identifier and its use in online services is generally associated with other types of information that make it possible to identify and profile the person holding such a key. Under these conditions, the public key is personal data that uniquely identifies a person and thus its processing is subject to the provisions of the GDPR, although it can be considered as a method of pseudonymisation insofar as it can conceal a person's real name.

In the application of cryptography, the use of a key is the determining parameter. There are many definitions of what a key is. Briefly, we can say that a key is a parameter that determines the result of a cryptographic algorithm. Depending on this key, encryption systems can be divided into two main groups: symmetric encryptions, where a single key encrypts and decrypts; and asymmetric encryptions, where two keys are required, one for encryption, which may be public, and another, for decryption, which is private and only in the possession of its legitimate owner. The two keys in asymmetric encryption are linked, but it is very difficult to deduce one from the other without additional information.
Asymmetric encryptions are designed so that one of the keys is revealed and freely accessible, the public key, which makes them very suitable for use on the Internet. Thus, the use of asymmetric keys not only allows the encryption/decryption of information, but also allows the authentication of persons, the generation or verification of signatures, exchange of symmetric keys, etc.
Public keys can be used by individuals, entities and even machines to identify themselves, authenticate themselves or exchange information. When it comes to public keys that correspond to natural persons, the question arises as to whether these keys can be considered personal data. In this respect, both the French authority CNIL (Solutions for a responsible use of the blockchain in the context of personal data) and the European Parliament (Blockchain and the General Data Protection Regulation) have already stated that they are personal data in the context of specific processing tasks.
In order to determine the personal data nature of the public key, a consideration must be given to the very definition of personal data as set out in Article 4:
‘personal data’ means any information relating to an identified or identifiable natural person (‘data subject’); an identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person
And Recital 30 of the GDPR details the interpretation of personal data in relation to online identifiers:
Natural persons may be associated with online identifiers provided by their devices, applications, tools and protocols, such as internet protocol addresses, cookie identifiers or other identifiers such as radio frequency identification tags. This may leave traces which, in particular when combined with unique identifiers and other information received by the servers, may be used to create profiles of the natural persons and identify them.
In this respect, the public key is a unique identifier by its very nature, since the probability that two people can share the string of characters that constitute a key is practically zero. If this were not the case, the scheme of security guarantees that is built on encryption systems over the Internet would not work.
On the other hand, the use of the public key in online processing is intimately linked to other types of identifiers, such as IP addresses, session identifiers, cookies, device signatures, e-mail addresses and others. All this information leaves its trace in the log or activity files of servers or intermediate agents. Moreover, the combined use of these identifiers, including the key itself, allows the activity performed from different addresses or devices to be associated.
The public key and the private key will make it possible to profile the person to the extent that they are used to prove that different online actions are linked to the same individual, e.g. in the case of authentication or Blockchain. This type of information can be so accurate that, in practice, it has also been used to successfully re-identify the person. In fact, activity-based re-identification has become a service available to various actors, such as law enforcement agencies.
In many cases, the public key is physically created by a third party other than the natural person to whom the key will be linked. This is the case of public key infrastructures (PKI), where the key creation and distribution process involves the reliable identification and registration of the natural person with the service provider or the designated registration authority, as well as the inclusion of personal information in a digital certificate. In some treatments, this authentication is required by law even if the public key is generated by the individual concerned (e.g. in virtual currency exchange or e-wallet custody services).
Of course, the public key will be linked to the content of the message and all its possible metadata when used to electronically sign a message to ensure its integrity.
Finally, the user of the public key has to keep a private key in his possession in order for the asymmetric encryption to work properly. Although one key cannot be deduced from the other, the association between the two keys can be demonstrated, since what is encrypted with one key can only be decrypted with the other. Therefore, it is possible to prove the link between the user and his public key in case of access to the user's secrecy, e.g. in the event of a personal data breach or by a court action.
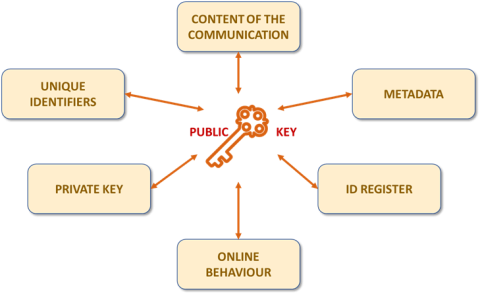
In short, in those processing operations in which it is possible to associate additional information to the public key that allows the identification of the person, the public key will act as a pseudonym with the consideration of personal data since, as defined in Article 4(5) of the GDPR, pseudonymised information is personal data.
More material on encryption and pseudonymisation issues can be found on the AEPD's Innovation and Technology page, in particular: