Personal data breaches: Ransomware and risk management
Ransomware is a cyber-threat with a high impact on personal data that is well known and increasingly common. Within the context of COVID-19, this type of attack is significantly affecting the processing of health-related data. Data controllers must implement specific measures, both of a preventive nature and contingency plans, in order to minimise the consequences of these attacks.

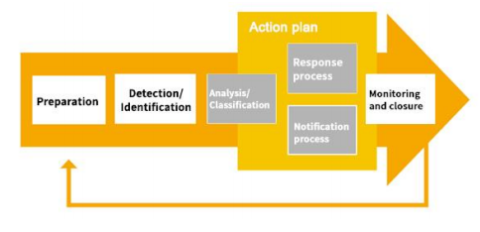
With regard to ransomware, it is necessary for data controllers and processors to be aware of the risk posed by these attacks, as they are increasingly common, as well as to implement appropriate technical and organisational measures to address them. These measures must be aimed at three levels: firstly, trying to prevent their materialisation; secondly, having the capacity for early detection and rapid assessment of the consequences; and, thirdly, minimising the impact on the rights and freedoms of the persons whose personal data are affected.
In order to fulfil this third aspect, it is no longer sufficient to have backups or other isolated safeguards. Where the availability of processing has a major impact on citizens, continuity plans must be established in order to ensure the provision of services to data subjects.
Continuity plans must address the increasingly common threat of ransomware, but must go beyond it. Organisations have implemented their ICT services with strategies that require high connectivity and numerous third parties involved. Consequently, they must have the resilience to face not only technical risks, but also all kinds of contingencies arising in the context of globalised information processing, such as political changes, regulatory changes or the discontinuity of products or applications. All of this makes it necessary to have an action plan and a business continuity plan based on the nature, scope, context and purposes of the processing, as well as the risks to rights and freedoms posed by the processing of personal data. These plans must enable an agile and precise response in a highly interdependent, dynamic and changing environment subject to legal, political, market, geostrategic and technical risks.
Ransomware is the product of a highly interconnected environment. This threat is a type of malware that prevents an organisation from processing data, usually by encrypting the data or the systems where they reside, and requests the payment of a ransom for the recovery of the availability of such data. It is a kidnapping of the information, since the person who legitimately should be able to process it cannot do so.
Ransomware is thus a threat not only to the availability of personal data but also to the service provided by processing such information, which may cause damage to the exercise of citizens' rights and freedoms. Indeed, sometimes ransomware is just the end point to other types of incidents that may go unnoticed for long periods of time, such as intrusions into information systems through different vulnerabilities or bad system configurations, compromising user credentials through phishing and/or obtaining access to systems through social engineering techniques. In this case, the confidentiality of personal data is also compromised and may lead to the sale of these data on the dark web. Among the different variants, some types of ransomware are directly aimed at password theft. While it is necessary to establish appropriate measures aimed at preventing a security breach and in any case at minimising its extent, equally important are the technical and organisational measures which, when adopted in advance, allow the availability of personal data to be re-established. It is not only a question of having backup procedures in place, but also of a comprehensive plan to re-establish the availability of the processing operations as a whole. These measures are key to ensuring business continuity, improving resilience and complying with the accountability requirements established in the GDPR.
All this without prejudice to any other obligations within the framework of different regulations, as well as the obligation to report this type of incident to the Law enforcement forces and agencies, since on most occasions they may constitute crimes. In this way cyber-criminals may be prosecuted. It is also important to seek assistance in the response from the relevant CSIRTs.
Initiatives such as the No More Ransom! project should be noted, which may sometimes facilitate the recovery of encrypted data. Paying blackmail to cybercriminals should not be considered as a possible option, but it is advisable to keep the information that has been encrypted in case tools can be developed in the future to decrypt this information.
In an era where data are the new “gold” of organizations, the impact of a ransomware-type security breach may be enormous and appropriate risk management and data governance strategies are key to determining precisely some relevant aspects of a security breach analysis and appropriate response, such as:
- categories of personal data affected
- number of records affected
- number of persons affected
- type of security breach (availability or confidentiality)
- If it affects availability, ability to re-establish it without causing any damage or level of potential damage
- If it affects confidentiality, actual risk of identification of persons and level of potential damage
The data controller must have such control over the systems in which he or she processes personal data that it allows to determine these parameters quickly and to assess the level of risk to the rights and freedoms of individuals.
The ability to determine this level of risk is key to being able to comply with the requirements of proactive liability established in the GDPR, which include:
- The obligation to notify personal data breaches to the supervisory authority, unless the breach is unlikely to pose a risk to the rights and freedoms of data subjects, within 72 hours of the data controller becoming aware that the event has occurred.
- The obligation to communicate personal data breaches to the data subjects in case of a probable high risk to their rights and freedoms. The purpose of such communication is to enable data subjects to adopt measures to protect themselves from the consequences.
For the notification of security breaches to the supervisory authority, the AEPD makes a form available to data controllers at its electronic office. In addition, to assist in making decisions on the need to notify a security breach to data subjects, the AEPD has published the Comunica-Breach RGPD tool.
You can obtain more information in the Guide on personal data breach management and notification, in the Innovation and Technology website of this Agency, as well as in our blog:


