Personal data breaches: online productivity platforms

Business email has evolved to become the gateway to productivity and office automation technology platforms in the cloud, through which much of an organisation's information - including personal data - flows. The potential for accessing all this strategic and confidential information has, in recent years, made these platforms more liable to attack by cybercriminals.
I. Email and cloud-based productivity and office automation platforms
Since it was invented in the 1960s, electronic mail has become popular in parallel with the accessibility of data communication networks and services, and is now one of the most widely used communication tools both in the workplace and in private life.
The traditional architecture on which email was hosted on an organisation's servers and managed by its own or external staff has, with the introduction of new technologies such as instant messaging and social networks, resulted in a situation where large technology multinationals' cloud computing resources are used. In turn, the use of email has grown in terms of functionality, from being a simple means of exchanging text-based messages to becoming a key part of an organisation's decision-making process by adding all kinds of extra features - such as cloud-based document sharing, video-conferencing, surveys, multimedia and so on.
As a result, organisations end up with large information repositories in the cloud that can be accessed using the same credentials as are used for email. The cloud stores and processes information, both current and historical, from public and private organisations, covering any sphere - from small businesses to large companies, and educational centres. This can create situations where organisations are technologically dependent.
This is the case for organisations that use products such as Microsoft's Office365 or Google Suite, which currently dominate the professional market.
II. Privacy risks
Access to these resources has clearly also evolved from requiring a company computer connected to its intranet for accessing email to the current situation where people are able to access from any device they have at hand with an internet connection - regardless of the network they are connected to, simply using a web browser and via a common site address for all organisations that use the same corporate platform. This is one of the advantages of holding the information in the cloud, but at the same time it represents an inherent risk in this technology.
This ease of connectivity has meant that the scope for attacking systems extends to the entire internet, with risks including:
- Attempts to access corporate platforms using brute force
- Attempts to access by reusing login details from other internet services whose security has been breached.
- Theft of login details using social engineering attacks - such as phishing, where the user ends up entering his or her corporate credentials into fraudulent websites controlled by the cyber attackers.
- Personal information becoming exposed due to there being no differentiation between tools used in the work and private settings.
As a way of combating this range of threats, measures must be implemented to minimise the likelihood of them occurring. Options for this include:
- Choosing reliable, guaranteed solutions and service providers, and paying attention to the configuration of security and privacy options offered by cloud productivity platforms.
- Setting out procedures and recommendations on accessing corporate tools when on the move and teleworking. These should be easy to understand and follow by all members of the organisation.
- Establishing restrictive policies on accessing corporate productivity tools for personal use or from non-work devices and, where this is permitted, establishing appropriate security measures and information-sharing mechanisms that keep personal and professional matters separate.
- Two-factor authentication: this is the measure that is most strongly recommended when accessing online services. Online office suites frequently offer the option of accessing their systems not only with a username and password, but with the added security of authenticating the user with a token, text message or app on another device.
- Strong passwords: the use of hard-to-guess passwords that are not used on other services is essential in protecting against improper access. A suitable policy regarding the correct use of passwords should be implemented across the organisation. We recommend checking the services that provide information about accounts that have suffered security breaches on other websites, in case any member of the organisation has reused their login details.
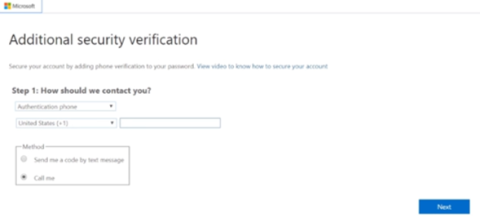
Image 1. Two-factor authentication with Office 365.
- Checking for improper access: correctly managing these portals' access logs can provide a lot of information; times of the day when they should not be accessed; geo-located IP addresses in places where the organisation has no presence; or regular access errors on some accounts can all provide clues to knowing if your organisation is being attacked in any way.
- Checking for email forwarding: once someone's login credentials have been compromised, one of the first things cybercriminals do is set up an email-forwarding rule to intercept your communications by forwarding your email to their mailbox. This enables them to analyse your information without having to access your mailbox. Depending on the office suite being used, this can be checked at administrator level in a variety of ways - such as this solution for Office365. In any event, users always have the option of checking to see if any forwarding rules have been set up and removing them.
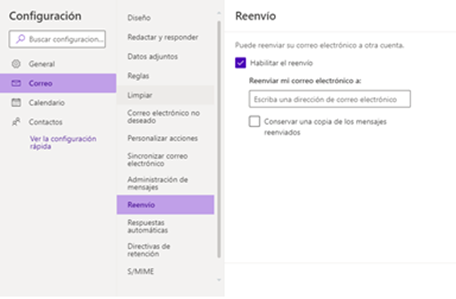
- Training the members of your organisation about the culture of data protection and security, emphasising the need to protect their credentials and stopping them from being reused, as well as the social engineering threats from their credentials being entered into fake home pages.
- Putting in place policies on the need for regular cancelling or blocking of data.
- Setting up automatic audit systems that raise an alert in the event of unexpected activity within the email system and halting certain activities.
This post is part of a special supplement on security breaches:
- Personal data breaches: protect yourself if you lose a portable device or it is stolen
- Personal data breaches: what they are and what to do
- Personal data breaches: protect yourself against ransomware
- Personal data breaches: communicating with data subjects
- Personal data breaches: Top 5 technical measures you need to take into account


