Personal Data Breach: Security Focused on Processing
The GDPR obligates controllers to implement appropriate technical and organisational measures to ensure an appropriate security level to the risk of processing.

Photo by Glenn Carstens-Peters at Unsplash.
The GDPR obligates controllers to implement appropriate technical and organisational measures to ensure an appropriate security level to the risk of processing. Therefore, the controller is required to assess the risks to the rights and freedoms of natural persons inherent in the processing and apply measures to mitigate them. Security focused on processing is a broader concept than security focused exclusively on systems.
It is worth remembering that GDPR’s scope of application is to process personal data, understood as processes with an ultimate and specific purpose, while the scope of application of other regulations, such as cybersecurity or the recently approved AI Act, are oriented to information and communications systems.
For example, National Security Framework (ENS Esquema Nacional de Seguridad) applies to both the public sector’s information system and to service providers within the private sector who also provide solutions to public sector entities.
However, the Royal Decree 311/2022, of May 3d, regulating the National Security Framework in its art. 3 specifies that when an information system is used for processing personal data, provisions of the GDPR and other applicable data protection regulations shall apply in each case.
Illustrating the difference is the case of access control operations in personal data processing. Unfortunately, it is relatively common for individuals to use same password or weak passwords across multiple services and applications. This allows third parties to use compromised credentials to simply log in to a service or application, and with them obtain more personal data about people and enrich other databases.
In cases where third party's actions do not go beyond logging in and obtaining personal data stored in different systems, some controllers incorrectly claim that a breach has not occurred within the meaning of the GDPR since, in their opinion, the security of the information system has not been compromised (security focused on systems). These controllers understand that the use of valid credentials to log in to the information system has not led to a personal data breach in the processing as the system has worked correctly.
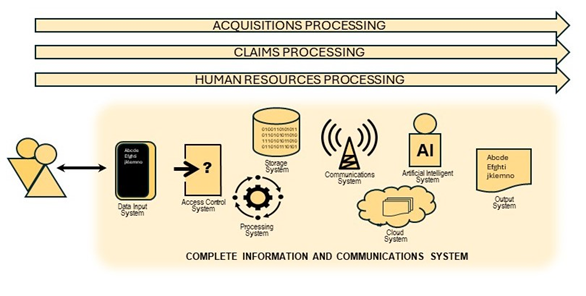
But analyzing the same event with the approach focused on processing established by the GDPR in its article 32, it is easy to reach the conclusion that these events represent a violation of the processing security, while the established security measures have not prevented the personal data access by unauthorized third parties without legitimacy. In short, the security measures have not been sufficient to guarantee the confidentiality of the personal data processed by the controller and a personal data breach has occurred in accordance with the definition established in art. 4.12 of the GDPR. The objective of art. 32 is to ensure that a breach does not occur in the processing of personal data that puts the rights and freedoms of natural persons at risk. If it is manifestly evident that an access control method has been chosen in the processing design that is vulnerable to spoofing beyond what is reasonable, the processing design is not sufficiently secure, no matter how well the considered systems behaved individually.
In such case, the controller will be obliged to manage the personal data breach, assess the risk and take the appropriate actions in accordance with articles 33 and 34 of the GDPR.
This post is related with other material released by the AEPD’s Innovation and Technology Division, such us:
- Personal data breaches: Ransomware and risk management
- Personal data breaches: online productivity platforms
- Personal data security breaches: Top 5 technical measures to be taken into account
- Data breach: communication to the data subject
- Data breaches: protect yourself against the loss or theft of a portable device
- Personal data breaches: what they are and how to respond
- Personal data breaches: protect yourself against ransomware