Encryption and Privacy III: Homomorphic encryption
In the framework of “Encryption and Privacy”, this article focuses on homomorphic encryption. This privacy by default technique is suitable for cases where a controller contracts a processor to carry out part of the processing and the controller wishes to ensure, from a technical point of view, that the processor is not able to access the data. Some concepts, schemes and possible uses will be explained.

The processing carried out by a controller of personal data is often performed on the basis of services provided by a processor. The computing model used can be the typical client-server model, cloud computing or a distributed processing arising out of the new forms of edge-computing. Likewise, an important part of the data collected by the applications in our personal devices end up being processed remotely at third-party servers.
Under a traditional scheme, the controller transfers the information to the controller in an encrypted way to preserve the confidentiality of the data during the transfer. Upon receipt of the data by the processor, the processor decrypts and processes the information.
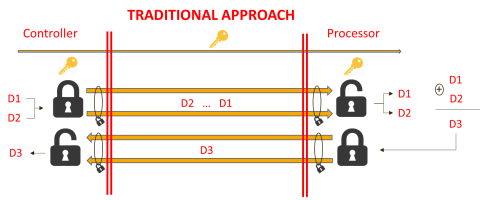
Figure 1 Under the traditional approach, data Dx communication is performed through a virtual tunnel that prevents access to the data that are circulating through such tunnel by means of encryption, which allows to create a confidential communication channel. Once received by the processor, the data are decrypted and processed.
To ensure that the data protection requirements are met in this model, two types of guarantees are set up: legal guarantees and technical guarantees. These two types of guarantees complement each other in order to manage the risk, and they must likewise be present at the time to process data that are outside the scope of the controller or the natural person that is using a remote service. Legal measures are laid down, inter alia, in Chapter IV of the GDPR, which provides for the relation between the controller and the processor.
These legal measures do not offer, per se, an absolute guarantee, for they can be limited by threats such as different legal scopes, changes in the regulation, illicit processing, breaches of the rule of law or security breaches.
Therefore, technical measures may be applied such like encryption solutions described in this post.
Analysing the traditional approach described above, in order to minimise the risks, the ideal solution could be that the processor would not be able to decrypt the information, and all the processing could be carried out on data encrypted by the controller. Therefore, a disloyal processor or third party that could access to the data wouldn’t be able to process the information. A way to achieve such level of data protection is through the so-called homomorphic encryption.
Homomorphic encryption is a technique that allows for operations to be carried out on encrypted data. The results of such operation are encrypted too and, more important, equivalent to the results obtained working with the original information directly. Figure 2 shows one of the possible cases in the use of this technique.
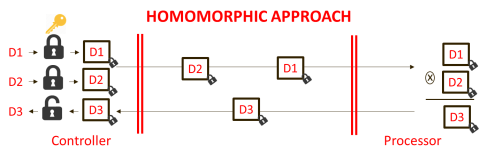
Figure 2 In this case, data Dx are encrypted one by one at the controller, the processor only needs to decrypt them to perform the operations. The symbol of the operation changes because an equivalent operator that produces equivalent results is used.
There are three types of homomorphic encryption: full or FHE (Full Homomorphic Encryption), somewhat or SHE (Somewhat Homomorphic Encryption), and partial, when the type of operations is limited, or PHE (Partial Homomorphic Encryption).
Homomorphic encryption is a very interesting Privacy by default measure, especially for the processing of special categories of personal data, by avoiding the access by the processor to the content of the information. Likewise, it has operating advantages, such as do not need to implement a key relation between the controller and the processor. Thus, the encryption system management of the controller is keeping apart from the external world.
Even a limited homomorphic encryption, such as the PHE, may have immediate applications to improve privacy. A specific case could be the collection of data from devices in Internet of Things (IoT) applications with the purpose of obtaining aggregated values. In such use case, the intermediate aggregator could receive individual encrypted data and add them up. The final data aggregator would only receive encrypted accumulated values. A very similar scheme may be used, for example, in electronic voting.
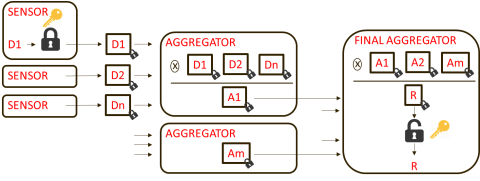
Figure 3 In this case of use, sensors encrypt each of the readings with a decryption key only shared with the final aggregator. Several levels of aggregators (in the figure, only one layer) may process and/or accumulate the values of the different sensors. These intermediate elements may perform a processing activity without accessing the original data. Only the destination has the key that allows access to the final result.
The use of homomorphic encryption opens new opportunities for the processing of data with higher guarantees, such as servers based on the IoT, Cloud Computing and automated learning or Machine Learning.
Notwithstanding, this technique still has several problems and it is not free from risks. For the time being, processing with homomorphic encryption are very costly from a computational point of view, but this circumstance is gradually having a lesser effect due to the evolution of technology and the increase in the power of the systems. Likewise, these techniques create encrypted texts of a bigger size, which entails a higher communication cost. This problem is also becoming less important due to the high bandwidth of the links of the data.
Another risk to be assessed is the fact of using the same key on the data that are going to be processed may entail a vulnerability in the encryption system. This problem worsens when a great volume of information is processed and is accessible for a long period. In order to mitigate such a problem, the use of an additional encryption layer in communications is essential together with the need to minimise the information encrypted under the same key, which must be limited to the groups of data that operate with one another.
For a partial or PHE homomorphic encryption, it is possible to use asymmetric encryption schemes such as RSA.

Figure 4 where Dx is the original data, E is the encryption function and Cx is the encrypted data. The RSA encryption raises the data to the power of “k” and returns the result module “n” in order to perform the encryption. In the text above, we can see that the multiplication of the encrypted data equals to encrypting the result of the multiplication of the original data.
There are encryption schemes that likewise allow for a full homomorphic encryption or FHE, such as lattice-based cryptography. These schemes add a level of noise throughout the set of operations performed. This feature, which may be regarded as a disadvantage in some applications, in other applications may be combined with the differential privacy techniques to offer an additional level of privacy.
Soon, we will see practical implementations of homomorphic cryptography, another way the encryption techniques help to keep data privacy.