IoT (I): What is IoT and which risks does it entail
Vehicles, toys, watches, kitchen robots, bracelets, heart rate and blood pressure meters, robotic vacuum cleaners, loudspeakers and televisions are only a few examples of connected devices which we have assumed as “normal” in just over a few years, simply by adding the adjective “smart”. This is the Internet of Things, usually known by its acronym IoT, which, together with Artificial Intelligence , Big Data and 5G form the group of the main interrelated technologies that will have the greatest impact in the near future. In most cases, the operation of such devices involves personal data processing, and the associated risks must be identified and managed.

Opinion 8/2014 of the Article 29 Working Party, now European Data Protection Board, defines IoT as such infrastructure in which multiple sensors are incorporated to common, everyday devices (“things”) in order to register, process, store and transfer data, and interact with other devices or system by using its network connecting capabilities. In many cases, such objects are associated to unique identifiers and process data of a personal nature.
In case of personal data processing of IoT devices for personal or home use, the GDPR also applies to data controllers and data processors that provide the necessary means to process personal data related with such personal or home activities (Whereas 18).
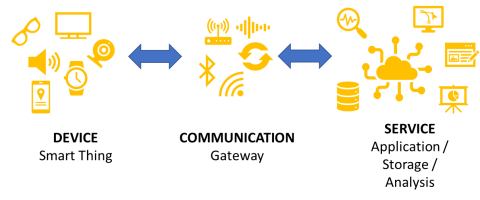
IoT solutions have a wide range of functions and are highly differentiated. Even so, they can loosely be described as having a three-layer architecture in which each distinct layer is capable of carrying out different personal data processing operations.
The first layer refers to the device or “thing” itself, which is specifically designed to perform four basic functions: collect, process, and communicate data, and interact with users. For the purposes of personal data processing, this layer mainly performs data collection operations. In such cases in which all data processing stage are locally developed at the device layer without involving all other layers, data processing would be included within the exception concerning household activities provided by the GDPR, since no actors external to the user device are involved.
The second layer is communications: it allows for exchange of data between the device layer and the service layer, or the exchange of data between devices. It includes the entire infrastructure which provides the means to enable this communication. For the purposes of personal data processing, this layer mainly performs bi-directional data communication operations.
The third layer is the service or application layer: it provides centralized analytical capabilities for processing data obtained from IoT solutions deployment. This layer services both the IoT device and other agents that take part in data processing. Nowadays, this service layer is offered from cloud infrastructures. This layer generally provides personal data processing and analysis operations.
Equally, in general terms, it is possible to speak about multiple actors involved in IoT solutions from each or several layers as mentioned above. For example, manufacturers and integrators of IoT, developers of IoT solutions, cloud services providers, data platforms, operating system developers, telecommunications operators, social media platforms, the advertising sector, etc. Depending on their intervention in personal data processing they may act as data processors or data controllers as provided by the GDPR, and such roles need to be perfectly identified in order to determine the responsibilities assigned to each of them.
The personal data processed by IoT devices include a wide range of categories, from basic contact data to geolocation, internet use habits, interest, physiologic data such as heart rate or body temperature, images, voice and many more. As for the source of such data, a common classification can be established applying to any IoT device: provided data, observed data, derivative data and inferred data.
Frequently, users are well aware that the data provided by them (provided data) or collected (data observed) by the IoT device by means of its sensors. However, the possibility of processing derivative personal data and inferred data are, in general, less known by users. Derivative data are those obtained by processing provided and observed data. Inferred data are those obtained from the analytical processing of a wide range of data, which involves data from many users and several sources. In those cases, very complex technologies such as Big Data, Artificial Intelligence and group privacy, mostly unknown for the average user, are involved.
The European Data Strategy published in February 2020 provides for the expected increase in the global volume of data, which shall be multiplied fivefold between 2018 to 2015, from 33 zettabytes to 175 zettabytes. It also provides for the changes in the data processing methods, and forecasts that by 2025 80% of data shall be processed by connected IoT devices, while in 2018 these data represented 20%.
In a non-exhaustive manner, the main risks to privacy and data protection, some widely covered by Opinion 8/2014 are listed below:
Invasive disclosure of profiles and behaviour patterns, provided that analyses based in information collected in an IoT environment enables to detect highly detailed and complete lifestyle and behavioural patterns of a specific person. This potentially allows to surveillance to the most private spheres of human live, and threatens to create situations where no privacy at all is to be expected. For example, smart doorbells or robotic vacuum cleaners are capable of sharing data, even your home’s floorplan, with large technology companies, or an insurer could obtain information on the driving habits of a connected vehicle and use such data to calculate the price of insurance or even to deny such insurance.
Lack of control and information asymmetry highlights the serious difficulties to allow data subjects to correctly revise data generated by them, excessive exposure and lack of control, which is even greater with respect to any subsequent use if data, especially derivative and inferred data.
Lack of transparency, linked to the fact that certain classic methods for obtaining consent are not easily applicable for some types IoT devices, may, in fact, render impossible to obtain valid consent or seriously affect the validity of other legal grounds. This is the case, for example, with small devices, with a very small display screen, without a speaker and, in sum, with little means to provide the user with information.
Participation of multiple actors with different degrees of controllership, joint-controllership or in the role of data processor, increases the risk of diluting responsibility or having asymmetries in the compliance level of each party. For example, some organization may be more vulnerable to attacks which may cause security breaches for personal data. The result is a situation of lack of control and lack of transparency, which is especially remarkable for derivative and inferred data and in the subsequent use of data. An example of this are the frequent integrations of smart devices with voice assistants.
IoT systems affect both its direct users and those which may find themselves nearby at some point, even if they have no intention of interacting with the system. Voice assistants are some of the devices which are more likely to entail this risk, since they might record conversations which are not intended to interact with the system.
Lack of appropriate security measures at any layer level, either due to the limitations of the devices themselves, or for deficiencies in the application of data protection principles from design, as non-encrypted communications, passwords by defect, etc. may have varying degrees of severity consequences, such as exploitation of device vulnerabilities which would allow its remote operation or malicious use against other devices, or direct attacks to the application layer which may be translated into a personal data breach and compromising users’ personal data.
Limitations to the possibilities to remain anonymous as soon as this service is used, not to say impossibility to remain anonymous. Linking IoT devices to unique identifiers, lined to the close links between certain devices and its users, make it virtually impossible to use such data anonymously, and the risk of re-identification skyrockets. For example, many devices, require user registration or include advertisement unique identifiers, such as smart televisions. Linking unique identifiers in mobile devices is a proven fact, and such devices are widely used to interact with and operate IoT devices.
In other words, the digital fingerprint of people is enlarged as many of their daily activities are “datified”. Considering the increasingly higher capacity to correlate, link and create cause-effect relationships, a fairly accurate and complete profile of a person can be drawn and not only about certain particular aspects but about the entire person.
Implementation of IoT based data processing required mature development models incorporating regulation requirements, standards and certification mechanisms which guarantee a certain level of protection of the fights and freedoms of the data subjects. Besides, just as users can enjoy certain series such as power or water supply, without an extensive knowledge in the subject, they should be able to use IoT solutions and trust that they are not threat to their privacy.
You may find further information about data protection and privacy on the Innovation and Technology website of this Agency, as well as on our blog:
Introduction to 5G Technologies and their risks in terms of privacy
GDPR compliance of processings that embed Artificial Intelligence. An introduction


