IoT (III): IoT Home Automation
Finding home elements that have converted into intelligent devices with an Internet connection is increasingly frequent. So much so that we often see this type of devices in catalogues of furniture shops and even of supermarkets quickly becoming part of our homes. Thus, it is necessary to pay attention and to understand the risks that may affect privacy and that may increase with an inadequate use of such devices.

The range of home automation IoT devices is always evolving. On and on, new products arise aimed at providing more comfortable services at home, services that can be handled from Apps installed in mobile devices or integrated within the voice assistant.
IoT is an evolution of traditional home automation where devices add a layer of intelligence and connectivity that enables them to better adapt to domestic needs. Some examples are motorised blinds, temperature and humidity sensors, smart bulbs, electronic locks, switches, or alarm call centres.
Most of these devices are designed in such a way that an Internet connection and access to cloud services are needed to manage them or to use them. The risks for privacy arising out of this phenomenon include more than just security problems. This IoT model entails the communication and the management of personal data by third parties, as well as the additional processing of personal data, such as the metadata of communication.
An IoT device generates a great amount of data that is submitted and processed by several services on the Internet so as to meet all user requests. Notwithstanding, many more other purposes could be used, such as, for example, the performance of behaviour profiling. Thus, the greater the number of services that process these personal data, the higher the risk for citizens. What is more, the integration of devices of several manufacturers could increase the risk, such as, when a different App needs to be used and a sign up must be completed for each manufacturer.
An example of risk materialisation, in this case due to a security breach, occurred in 2016, when the most harmful DDoS attack occurred for a lack of security updates in these devices. Other examples could be the kidnapping of home devices and control by third parties, or personal data breaches.
Devices such as spyholes or locks that are controlled from Apps installed in mobile phones entail the processing of images, videos, audios, and information on people’s habits. This information, together with other data pertaining to persons, may be used for profiling, and several additional purposes.
Smart devices implement several ways of connectivity. The most frequent are:
- Distributed connection: Devices are connected directly to a WiFi router that works as a gateway towards the manufacturer's cloud and is managed through their own App. The connection is individual, with the use of protocols such as HTTP and HTTPS. Some examples of these devices are IP cameras, some smart plugs, or electronic spyholes.
- Centralised connection: devices are connected through a hub or gateway that centralises communications, such hub being the sole device that is connected to the Internet directly. In this case, communications usually use specific wireless home automation protocols such as Zigbee and Z-wave and, to a lesser extent, Bluetooth.
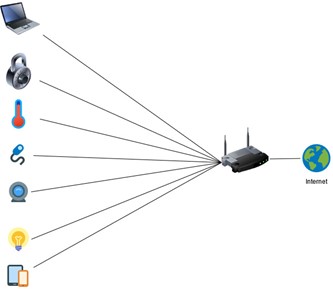
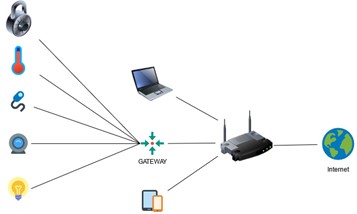
Given the diversity of options available, one single dwelling often includes devices manufactured by different manufacturers, which leads to a heterogeneous mix of the settings above.
In the near future, a massive adoption is expected of IoT devices connected to the manufacturer’s cloud by way of the 5G, which will be accessed through an App. This new way of connecting IoT devices could lead to new risks for the privacy of individuals. More information can be obtained on the risks of 5G at the Note: Introduction.
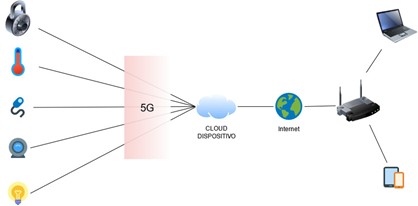
At a level of internal communications within home automation devices, both Zigbee and Z-Wave are the most widely used standards among the different manufacturers, and sometimes both standards can be found in one single device. These protocols are often included as a functionality as well in smart speakers or SmartTVs thus allowing for their full integration with the rest of IoT devices at home. Zigbee and Zwave have several years of use and evolution, but they are not exempt of or settings.
Zigbee is an open standard devised so that devices consume little energy. They minimise the submittal of information, spending most of the time in a latent state collecting data. This makes it possible to have up to 65,000 devices such as temperature sensors, door or window sensors that can provide a service for many years with only a coin cell battery. There are also other devices such as smart plugs, door engines, or bulbs that use this protocol through an electric network. The devices in our home make up a Zigbee network. It runs at 2.4GHz and exchanges information with the gateway. The wireless range is of up to 20 meters. Likewise, devices connected to an electric network operate as repeaters for battery devices.
Z-Wave is a proprietary standard that is similar to Zigbee. Some differences are the number of devices within a network, which becomes 232. The frequency for Europe is 868MHz and the wireless coverage is of up to 100 meters. It also has an architecture where devices plugged to an electric network provide a service for battery devices.
It is important for people to become sensitive on the fact that smart devices are something more than just a traditional household appliance. They will interact in people’s daily tasks by performing a great amount of processing activities. At the time to purchase these devices, a critical and demanding approach needs to be adopted vis-à-vis the guarantees of privacy. The selection criteria will need to be based on something more than the price or the main characteristics that are being offered. The user will need to verify that sufficient guarantees are provided on their personal data.
Manufacturers and developers need to apply data protection measures by default and by design. The processing performed will need to comply with the GDPR principles, with special attention to the security of processing activities, the possible international transfers of data, the transparency regarding the purposes for which personal data are to be processed, and the existence of profiling and individualised automated decisions. More precisely, the use of protocols needs to be avoided that use by-default encryption passwords, and which are public, or the possibility to add devices to the network automatically, beyond the data subject’s control.
You may find further information about data protection and privacy on the Innovation and Technology website of this Agency, as well as on our blog:
- IoT (I): What is IoT and which risks does it entail
- IoT (II): From The Internet of Things To The Internet of Bodies
- Connected vehicles
- Group privacy
- Data protection and security


